Overview
Best practices for data connection are paramount in ensuring security and compliance during integration processes. How can organizations effectively safeguard their data while meeting regulatory demands? This article underscores the necessity of implementing robust encryption, stringent access controls, and conducting regular audits. Such measures not only protect sensitive information but also ensure adherence to critical regulations like GDPR and HIPAA.
As a result, these practices significantly enhance both security and operational efficiency in data management. By prioritizing these strategies, organizations can confidently navigate the complexities of data integration.
Introduction
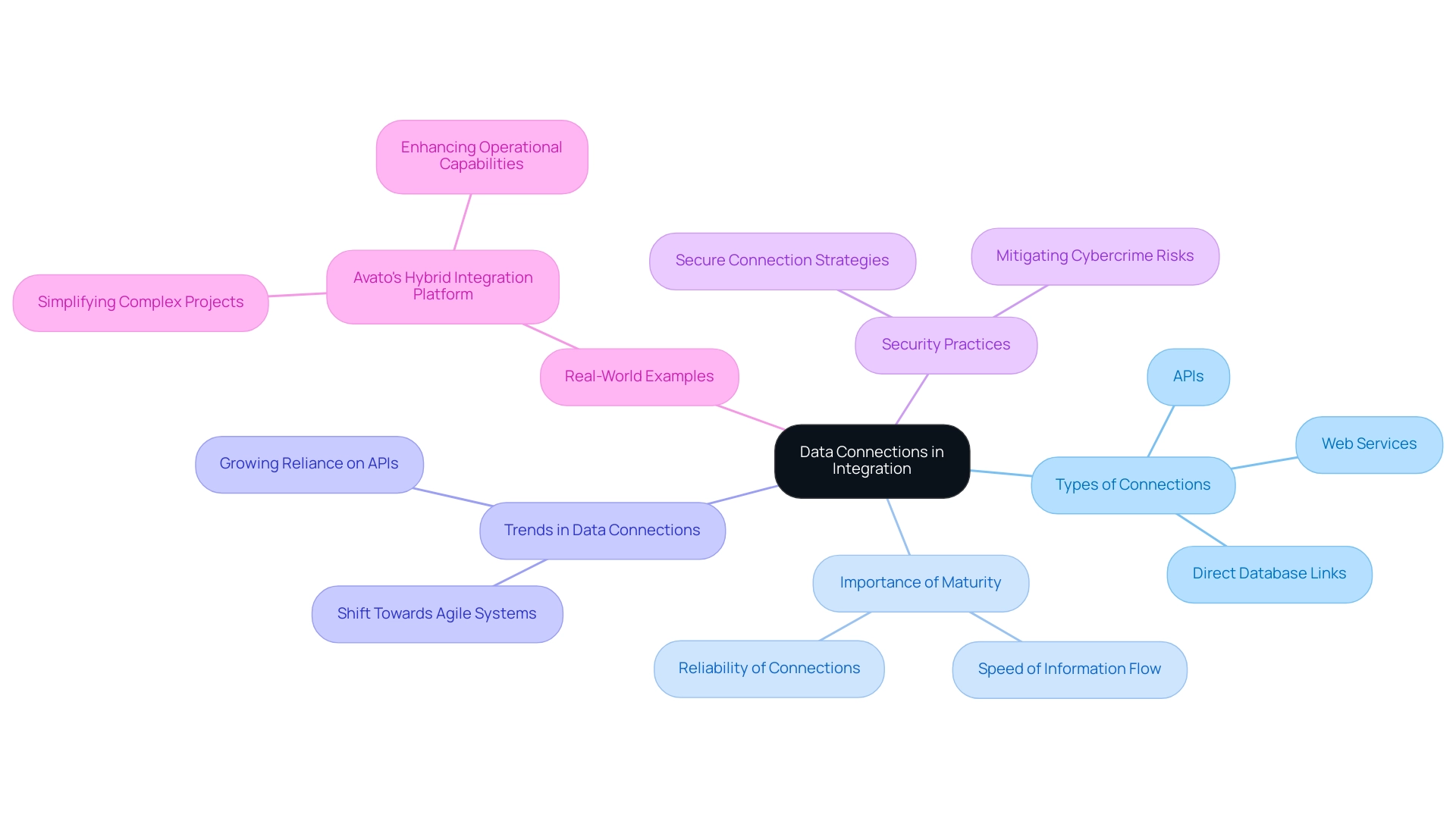
In the digital age, where seamless communication between systems is paramount, understanding data connections emerges as a critical factor for organizational success. These connections—encompassing APIs, web services, and direct database links—serve as the backbone of integration strategies, enabling efficient data exchange and optimizing operational workflows.
As businesses strive to navigate the complexities of modern technology, the significance of choosing the right connection types and prioritizing their maturity cannot be overstated. With a growing reliance on real-time data and secure practices, organizations must adopt robust strategies to enhance performance while ensuring compliance with ever-evolving regulations.
This article delves into the intricacies of data connections, offering insights into best practices, security measures, and optimization techniques that empower enterprises to thrive in a competitive landscape.
Understanding Data Connections: The Backbone of Integration
Data connections serve as essential conduits that facilitate communication and information sharing among disparate systems. In the realm of integration, a comprehensive understanding of various information link types—such as data connections, APIs, web services, and direct database links—is crucial. Each connection type, including data connection, serves distinct purposes, offering unique advantages and limitations.
For instance, APIs are widely recognized for facilitating real-time information exchange, a necessity for applications requiring immediate updates. Conversely, batch processing may be more suitable for transferring less time-sensitive information, allowing organizations to optimize resource usage.
As businesses navigate their unification strategies, assessing specific needs becomes paramount. The maturity of data connections plays a critical role in determining the speed and reliability of information flow. Entities that emphasize relationship maturity can significantly enhance their unification processes, leading to quicker and more reliable outcomes.
Indeed, companies that adopt advanced information linking practices often experience marked improvements in operational efficiency and reduced costs.
Recent trends indicate a growing reliance on APIs and web services for information unification, reflecting the industry’s shift toward more agile and responsive systems. By 2025, statistics suggest that over 70% of businesses will employ APIs as a key approach for information links, underscoring their significance in contemporary frameworks. Furthermore, expert insights highlight that understanding the nuances of these relationships is essential for effective integration, as they directly impact system communication and overall performance.
As Shivbhadrasinh Gohil, Co-founder & Chief Marketing Officer, observes, “Grasping information relationships is vital for successful unification, as they constitute the foundation of efficient system communication.”
Moreover, the importance of secure connection practices, particularly concerning data connections, is underscored by alarming statistics regarding cybercrimes reported to the ACSC in Australia, tracked from FY 2020 to FY 2023. This emphasizes the urgent need for organizations to implement secure strategies for data connections to mitigate risks associated with digital transformation. Avato’s hybrid unification platform addresses these challenges by employing robust security protocols that ensure the integrity and confidentiality of data connections throughout the unification process.
Real-world examples demonstrate the effectiveness of robust data connection strategies. Avato’s hybrid connection platform has been instrumental in assisting organizations in establishing data connections that streamline complex projects, enabling them to achieve desired results within tight timeframes and budget constraints. This capability not only enhances operational capabilities but also positions businesses to adapt swiftly to evolving market demands.
By optimizing the value of legacy systems and ensuring round-the-clock availability and dependability, Avato empowers banking IT managers to secure their operations for the future through seamless data connections and system unification. Avato’s commitment to simplifying complex connections further reinforces its dedication to delivering effective solutions that meet the needs of modern enterprises.
Additionally, the implementation of EDM practices is crucial for leveraging information as a valuable resource in the digital age, reiterating the overarching message regarding the significance of data connections in contemporary unification strategies.
In summary, the importance of data connection links in unification cannot be overstated. By utilizing appropriate relationship types and focusing on maturity, entities can ensure secure, efficient, and compliant processes that foster innovation and competitive advantage.
Prioritizing Security in Data Connections: Best Practices
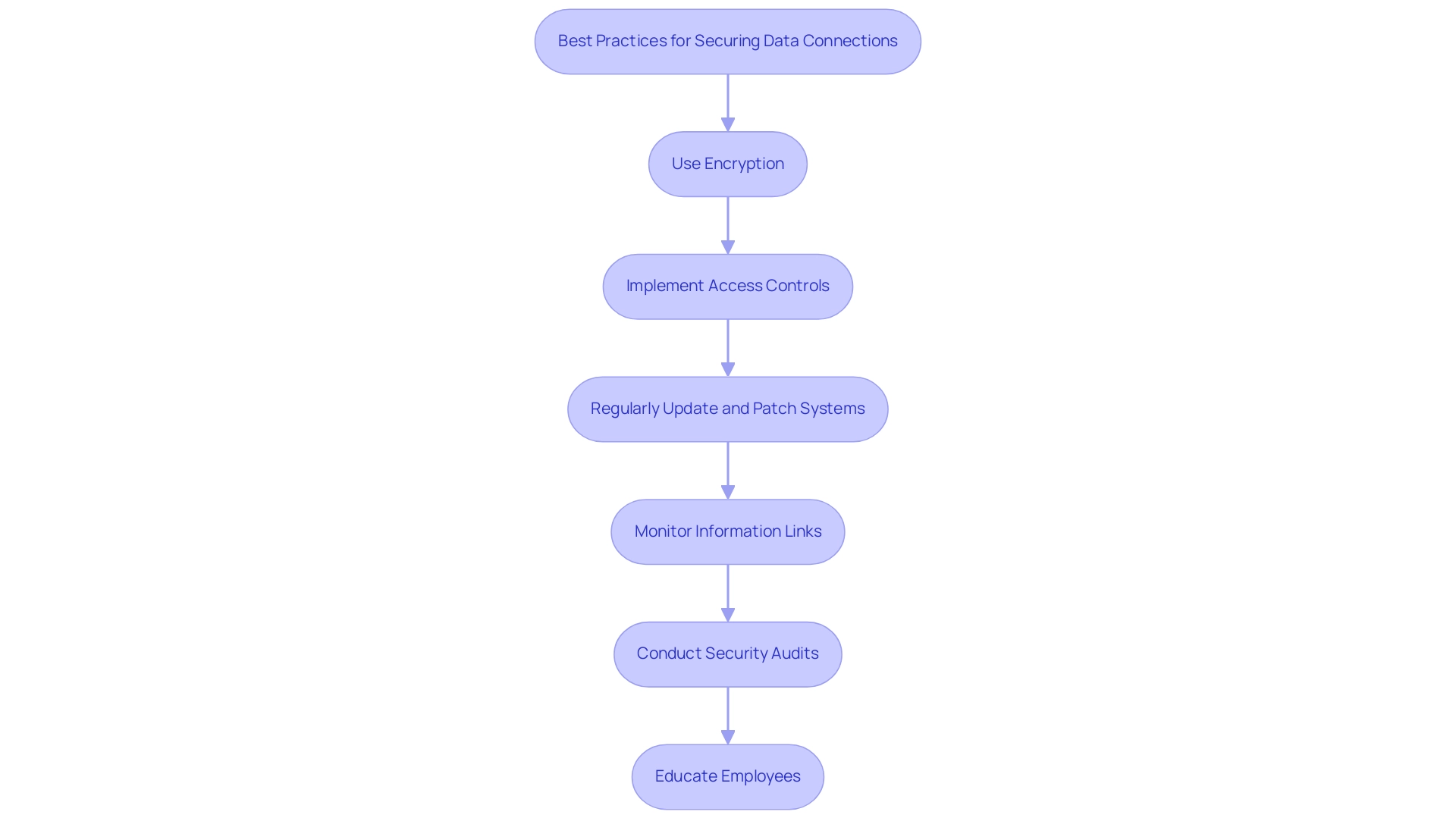
To ensure the security of data connections, organizations must adopt several best practices that are essential in today’s evolving cybersecurity landscape, particularly when implementing Avato’s hybrid integration platform.
-
Use Encryption: Encrypting information both in transit and at rest is critical for safeguarding sensitive content from unauthorized access. Employing robust protocols such as TLS for information in transit and AES for information at rest is essential to maintain confidentiality and integrity.
-
Implement Access Controls: Adopting the principle of least privilege is vital. By limiting access to information links according to user roles, organizations can greatly reduce the risk of unauthorized access and possible information breaches, thus improving overall security through a secure data connection.
-
Regularly Update and Patch Systems: Keeping software and systems up to date is crucial for defending against vulnerabilities. Regular application of patches and updates can thwart exploitation attempts by cybercriminals, ensuring that systems remain resilient against emerging threats.
-
Monitor Information Links: Ongoing surveillance of information links is essential for identifying irregularities and possible security risks in real-time. Implementing comprehensive logging and alerting mechanisms provides valuable insights into unusual activities, enabling swift responses to potential breaches through a secure data connection.
-
Conduct Security Audits: Regular security audits and assessments are essential for identifying weaknesses in data connection security. Engaging third-party experts to conduct thorough evaluations can uncover vulnerabilities and recommend necessary improvements, ensuring a proactive security posture.
-
Educate Employees: Training staff on security best practices and the significance of information protection is crucial. Investing in comprehensive training programs ensures that employees are comfortable with Avato’s hybrid integration platform and understand their role in maintaining security. Human error remains a leading cause of breaches; therefore, fostering a culture of security awareness can significantly reduce risks associated with employee actions.
In light of recent trends, such as the rise in ransomware attacks employing sophisticated obfuscation techniques, the importance of these practices cannot be overstated. Rajiv Gupta, Head of the Canadian Center for Cyber Security, emphasizes, “After all, we all have a role to play in building a safer, more secure Canada.” Statistics indicate that cybersecurity spending among small businesses is rising, driven by increased awareness of threats and the need for better defenses.
For instance, the fallout from the FBCS breach, which exposed sensitive information of over 4 million individuals, underscores the critical need for effective monitoring and response protocols. By adopting these best practices, entities can create a robust security framework that not only safeguards their data connection but also guarantees adherence to industry regulations.
Ensuring Compliance with Data Regulations
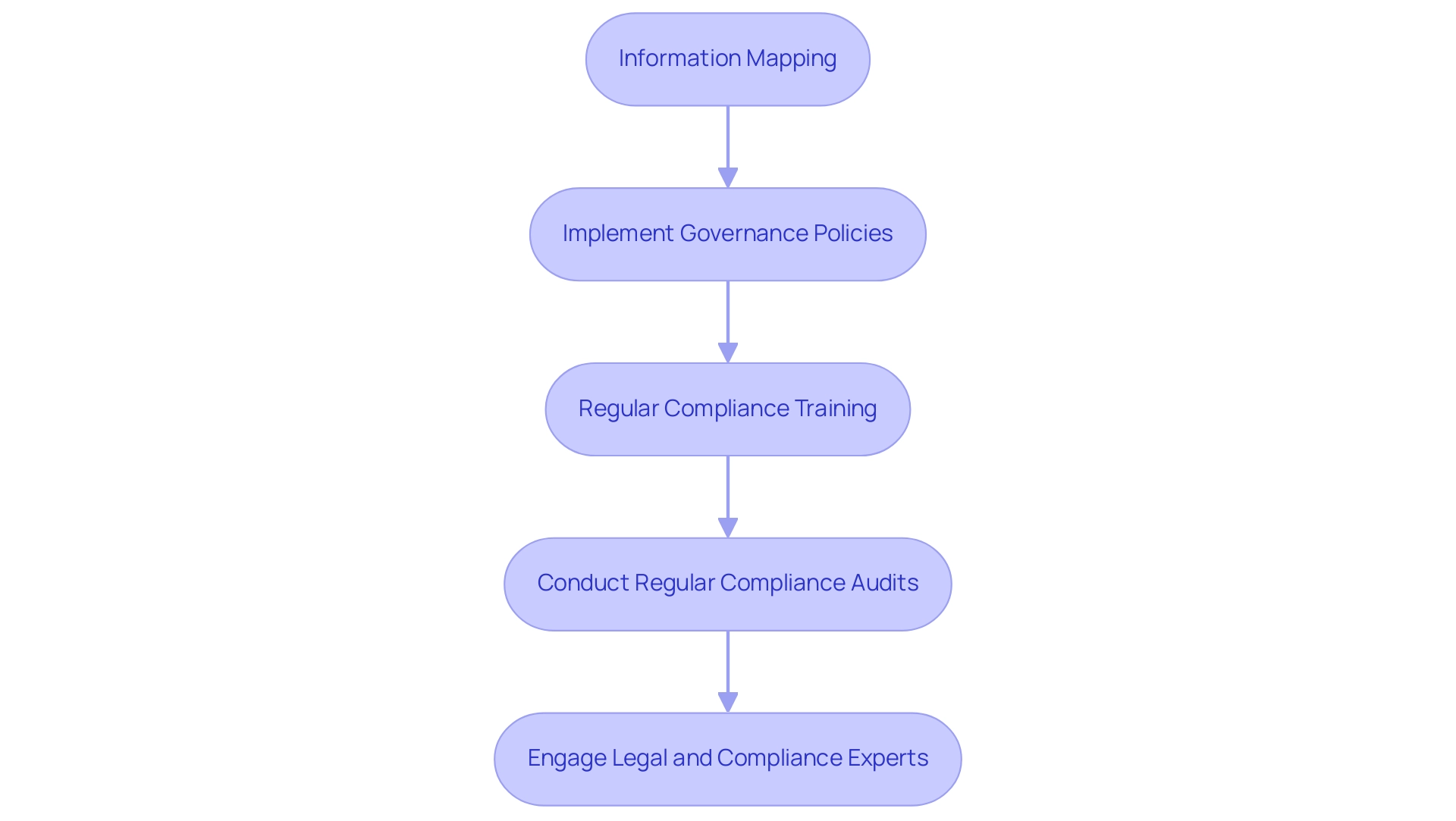
Adherence to protection regulations such as GDPR, HIPAA, and PCI DSS is not just important; it is essential for organizations managing sensitive information. To ensure compliance, consider these critical steps:
- Information Mapping: Begin with a comprehensive information mapping exercise. This process clarifies the types of information collected, processed, and stored, helping to identify specific compliance obligations.
- Implement Governance Policies: Develop robust governance policies that define information management practices, access controls, and protective measures. Clearly outlined roles and responsibilities are vital for effective governance.
- Regular Compliance Training: Ongoing training programs for employees on compliance requirements and best practices are crucial. This ensures that all staff members understand their responsibilities in maintaining compliance and safeguarding sensitive information.
- Conduct Regular Compliance Audits: Schedule periodic audits to evaluate adherence to protection regulations. These audits are instrumental in identifying gaps and areas for improvement, assisting organizations in maintaining compliance over time.
- Engage Legal and Compliance Experts: Collaborate closely with legal and compliance professionals to stay informed about regulatory changes, ensuring that data handling practices align with current laws.
By prioritizing adherence to regulations, organizations can significantly reduce the risks associated with information breaches. A case study titled “Leading Causes of Breaches” reveals that breaches often stem from weak passwords and insider threats, underscoring the necessity for businesses to enhance their protection measures, particularly in vendor management and access controls. Alarmingly, 27% of security and IT professionals cite mitigating internal audit fatigue as a top compliance challenge, highlighting the urgency for effective strategies.
Moreover, 77% of compliance experts recognize the importance of staying informed on ESG advancements, reflecting the evolving landscape of protection. As Sharavanan noted, ‘91% of business leaders believe their company has a duty to address ESG issues,’ emphasizing the broader accountability organizations have toward compliance and information protection. Successful mapping initiatives serve as real-world examples of achieving compliance, ultimately fostering a strong reputation for information protection.
In this landscape, Avato distinguishes itself by offering speed, security, and simplicity in integration—crucial elements for organizations striving to meet compliance requirements efficiently and effectively.
Optimizing Data Connections for Performance
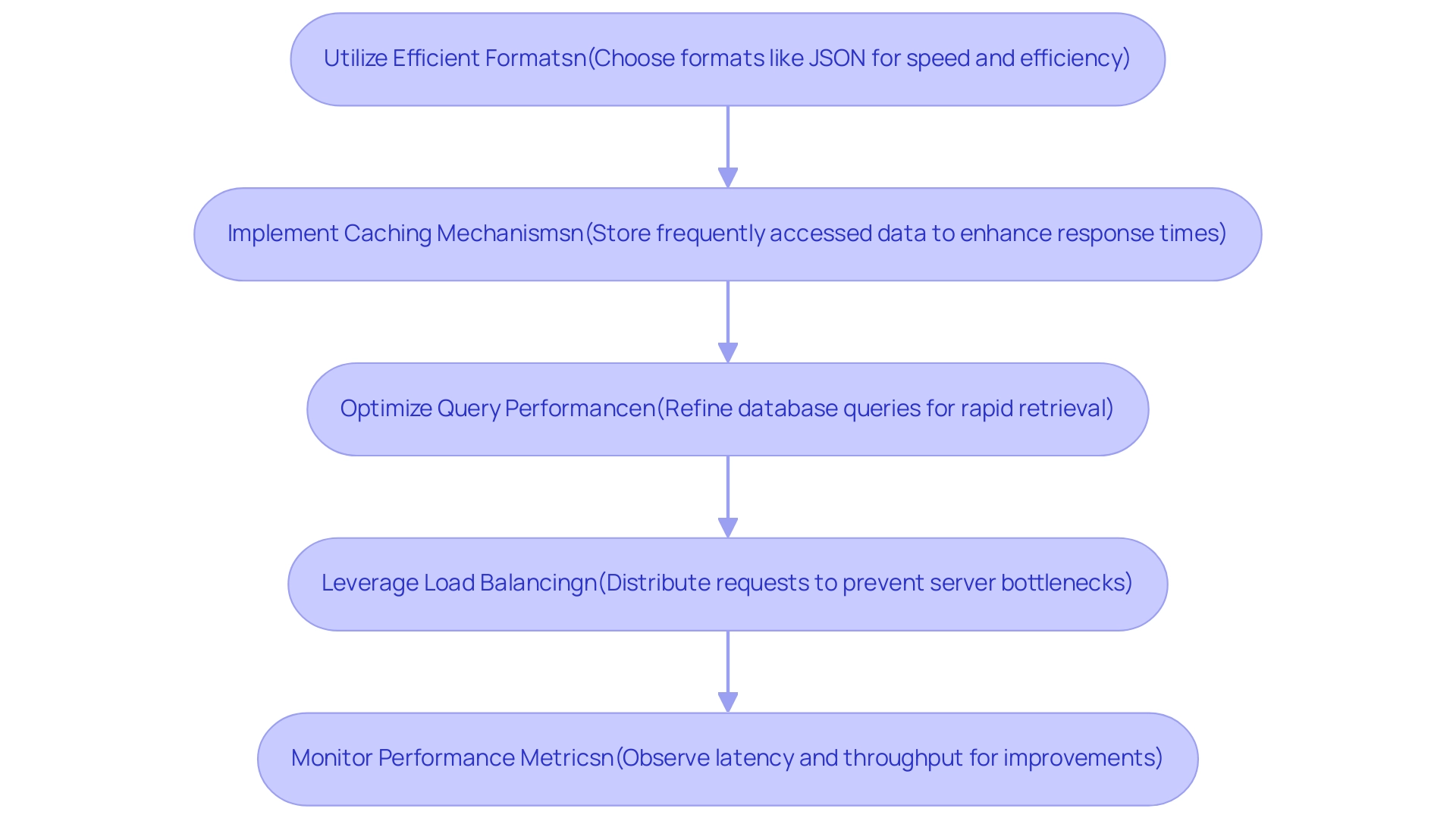
To enhance the performance of data connections, organizations must adopt effective strategies:
-
Utilize Efficient Formats: Selecting formats that prioritize speed and efficiency—like JSON or Protocol Buffers—can significantly reduce transmission overhead. JSON, in particular, has gained traction in enterprises due to its lightweight structure and ease of use, making it ideal for web applications and nested information scenarios. One key advantage of JSON over XML is its reduced markup, which simplifies parsing and enhances readability, making it a preferred choice for developers in hybrid integration environments. User manuals frequently recommend JSON for quick information interchange, while XML is better suited for rich metadata and validation needs. The choice of format should depend on application requirements, with CSV excelling at flat structures, JSON for web and nested formats, and XML for rich metadata and validation.
-
Implement Caching Mechanisms: Storing frequently accessed information can dramatically enhance response times by minimizing the need for repeated retrieval from the source. Real-world examples illustrate that effective caching mechanisms can significantly improve access speed, enabling organizations to respond to user requests more swiftly.
-
Optimize Query Performance: Regularly reviewing and refining database queries is crucial for maintaining efficiency. This includes practices such as indexing, minimizing unnecessary joins, and employing optimal query structures to ensure retrieval is as rapid as possible.
-
Leverage Load Balancing: Distributing requests evenly across servers through load balancing prevents any single server from becoming a bottleneck. This strategy not only enhances overall system performance but also ensures that resources are utilized effectively, supporting high availability and reliability. Avato guarantees 24/7 uptime for critical integrations, emphasizing the significance of reliability in connections.
-
Monitor Performance Metrics: Ongoing observation of performance metrics associated with connections—such as latency and throughput—allows organizations to identify areas for enhancement. By examining this data, informed decisions can be made regarding infrastructure upgrades and optimizations.
By prioritizing these performance enhancement strategies, organizations can ensure their data connections are robust and capable of meeting operational demands efficiently. As Gustavo Estrada observed, ‘Avato streamlines intricate projects and produces outcomes within preferred timelines and financial limits,’ underscoring the effectiveness of these tactics in improving information integration performance. Furthermore, with the evolving role of Chief Data Officers (CDOs) in driving AI initiatives, optimizing data connections becomes increasingly vital in the context of modern data leadership.
Conclusion
Understanding the intricacies of data connections is essential for organizations aiming to thrive in today’s digital landscape. This article highlights the critical roles of APIs, web services, and direct database links as foundational elements of successful integration strategies. Each connection type offers unique benefits, making it imperative for businesses to assess their specific needs and prioritize the maturity of these connections to enhance operational efficiency and reduce costs.
Moreover, the importance of security cannot be overlooked. As cyber threats continue to escalate, implementing best practices such as:
- encryption,
- access controls,
- regular system updates
is crucial for safeguarding sensitive data. Organizations that proactively address security measures not only protect their assets but also ensure compliance with evolving regulations, thereby minimizing the risks associated with data breaches.
Furthermore, optimizing data connections for performance is a strategic necessity. By adopting efficient data formats, caching mechanisms, and load balancing, companies can significantly enhance their operational capabilities. Continuous monitoring and refinement of these processes will ensure that data connections remain robust and responsive to the demands of modern business environments.
In conclusion, as organizations navigate the complexities of digital integration, the focus must remain on leveraging the right connection types, ensuring security, and optimizing performance. By doing so, enterprises can drive innovation, maintain compliance, and secure a competitive advantage in an increasingly interconnected world. Embracing these strategies will empower businesses to adapt and excel, ensuring their success in the digital age.

