Overview
Successful integration of computer systems hinges on three pivotal practices:
- Establishing robust security protocols
- Streamlining legacy system integration processes
- Implementing real-time monitoring and performance evaluation
What’s holding your team back from achieving seamless integration? We understand the complexities involved, and that’s why we emphasize specific strategies such as:
- Risk assessments
- Middleware solutions
- The use of KPIs
These elements are not merely suggestions; they are essential for ensuring secure, efficient, and effective integration of diverse computer systems across various sectors. By adopting these practices, we can enhance operational efficiency and safeguard your data integrity. Let’s work together to transform your integration challenges into streamlined solutions.
Introduction
In today’s landscape, digital transformation is not merely a choice; it is an imperative. Organizations must confront the urgent challenge of integrating legacy systems with modern technologies, all while ensuring robust security and operational efficiency. As we strive to remain competitive, the demand for effective security protocols, streamlined integration processes, and real-time monitoring has reached critical levels. This article explores essential strategies we can adopt to safeguard our data integrity, enhance system interoperability, and optimize performance across various sectors, including banking, healthcare, and government.
By leveraging innovative solutions like Avato’s Hybrid Integration Platform, we can not only mitigate risks but also unlock new opportunities for growth and customer engagement in an increasingly complex digital landscape.
What’s holding your team back from embracing this transformation? Let’s explore how we can navigate these challenges together.
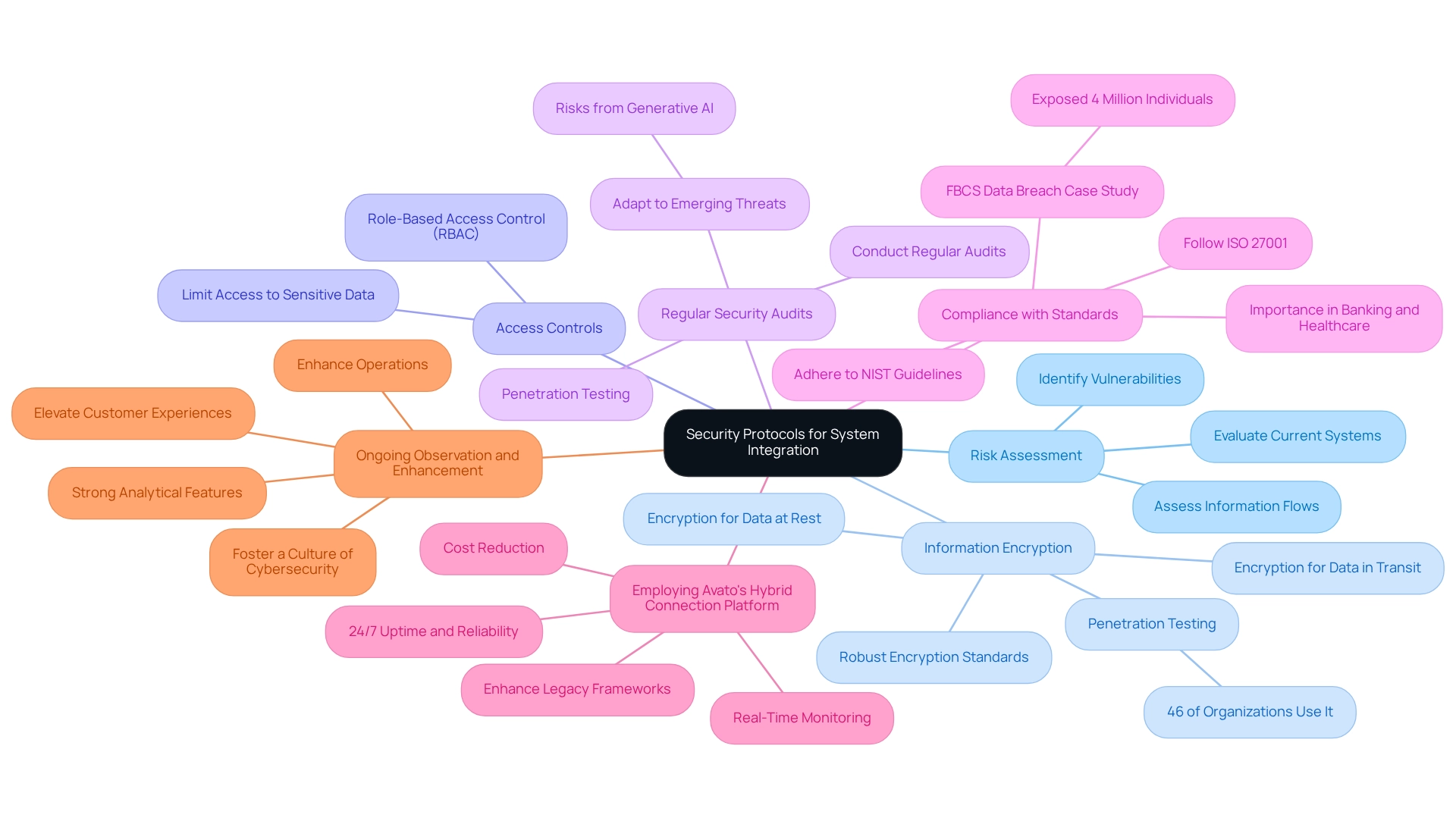
Establish Security Protocols for System Integration
To establish effective security protocols for integration, we must conduct a thorough risk assessment to identify potential vulnerabilities. This assessment should evaluate current systems, information flows, and access points. Key practices include:
-
Information Encryption: We implement robust encryption for all information in transit and at rest, utilizing strong encryption standards. This is crucial for safeguarding sensitive information against unauthorized access, especially as 46% of organizations rely on penetration testing to assess vulnerabilities in APIs before deployment. The financial implications of security failures are significant; the average total cost of a mega breach, which can involve 50-60 million records, is approximately $332 million.
-
Access Controls: We adopt role-based access control (RBAC) to limit access to sensitive systems and data. This guarantees that only permitted individuals can reach essential connection points, improving overall security.
-
Regular Security Audits: We perform regular audits and penetration testing to uncover and address security weaknesses. This proactive approach is essential for maintaining a secure integration environment and adapting to emerging threats, particularly with the rise of generative AI technologies, which introduce new risks that we must be prepared to manage.
-
Compliance with Standards: We follow industry standards such as ISO 27001 or NIST guidelines to ensure that our security practices align with regulatory requirements. This adherence is crucial in areas such as banking and healthcare, where information integrity is paramount. The recent data breach experienced by FBCS in February 2024, which exposed sensitive information of over 4 million individuals, underscores the critical need for stringent security measures.
-
Employing Avato’s Hybrid Connection Platform: We utilize Avato’s platform to enhance and expand the value of legacy frameworks while simplifying intricate connections. The platform’s features for real-time monitoring and alerts on performance ensure that we can maintain 24/7 uptime and reliability, which is essential for critical sectors like banking, healthcare, and government. Furthermore, the platform greatly lowers expenses related to incorporation, making it a valuable resource for organizations.
-
Ongoing Observation and Enhancement: We ensure our solution provides strong analytical features to continuously assess the performance of our hybrid setup. We utilize these insights to enhance operations, elevate customer experiences, and discover new avenues for innovation. By prioritizing these security measures and employing Avato’s Hybrid Integration Platform, we can effectively reduce risks related to the integration of computer systems, thereby safeguarding our data integrity and improving our overall cybersecurity stance. The shared responsibility of cybersecurity emphasizes that all employees play a role in safeguarding digital assets, fostering a culture of collective action to bolster defenses.
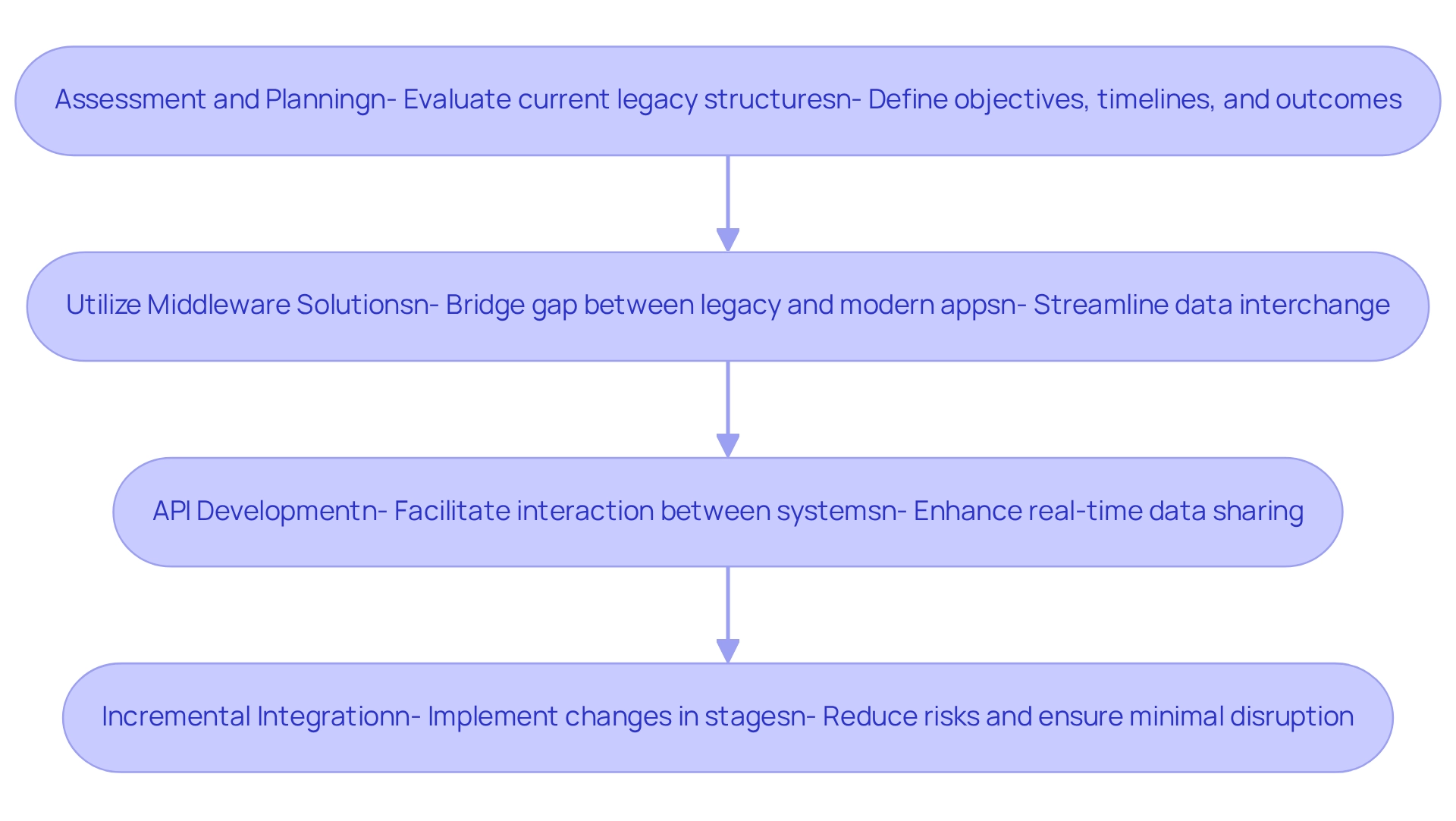
Streamline Legacy System Integration Processes
To streamline the integration of legacy systems effectively, we must adopt a structured approach that encompasses several key practices:
- Assessment and Planning: We begin with a comprehensive evaluation of current legacy structures to identify their strengths and weaknesses. Establishing a clear strategy for the integration of computer systems is essential, defining our objectives, timelines, and expected outcomes.
- Utilize Middleware Solutions: We leverage middleware to bridge the gap between legacy technologies and modern applications. Middleware streamlines data interchange, alleviates compatibility challenges, and is increasingly preferred; nearly half of organizations opt for hybrid cloud solutions when replacing outdated infrastructures. As Rituparna, a Tech Writer, observes, “In a digital world, decision speed is frequently your greatest asset,” emphasizing middleware’s critical role in accelerating connection processes. Avato’s hybrid integration platform exemplifies the integration of computer systems by providing a secure and efficient foundation for connecting diverse networks across banking, healthcare, and government sectors.
- API Development: We develop APIs that facilitate seamless interaction between legacy systems and new applications. This enables real-time data sharing, enhancing interoperability and responsiveness to market demands. The incorporation of generative AI further enhances these capabilities, allowing for sophisticated customer engagement through advanced chatbots and virtual assistants, ultimately improving customer experience.
- Incremental Integration: Instead of aiming for a total overhaul, we consider an incremental integration strategy. By incorporating frameworks in stages, we can reduce risks and implement necessary changes based on continuous feedback. This approach not only updates legacy infrastructures but also guarantees minimal disruption to operations through the integration of computer systems, ultimately enhancing customer experiences and preserving brand trust in a competitive environment. Innovations in fintech have been designed to improve customer-facing processes, including KYC compliance and personalized recommendations, which are crucial for traditional banks to remain competitive. These enhancements streamline customer interactions and engagement, allowing banks to adapt to the evolving market and meet customer expectations effectively. Digital progression is essential for mortgage lenders to remain competitive and improve borrower experiences.
- Contact us to learn how we can support your integration needs.
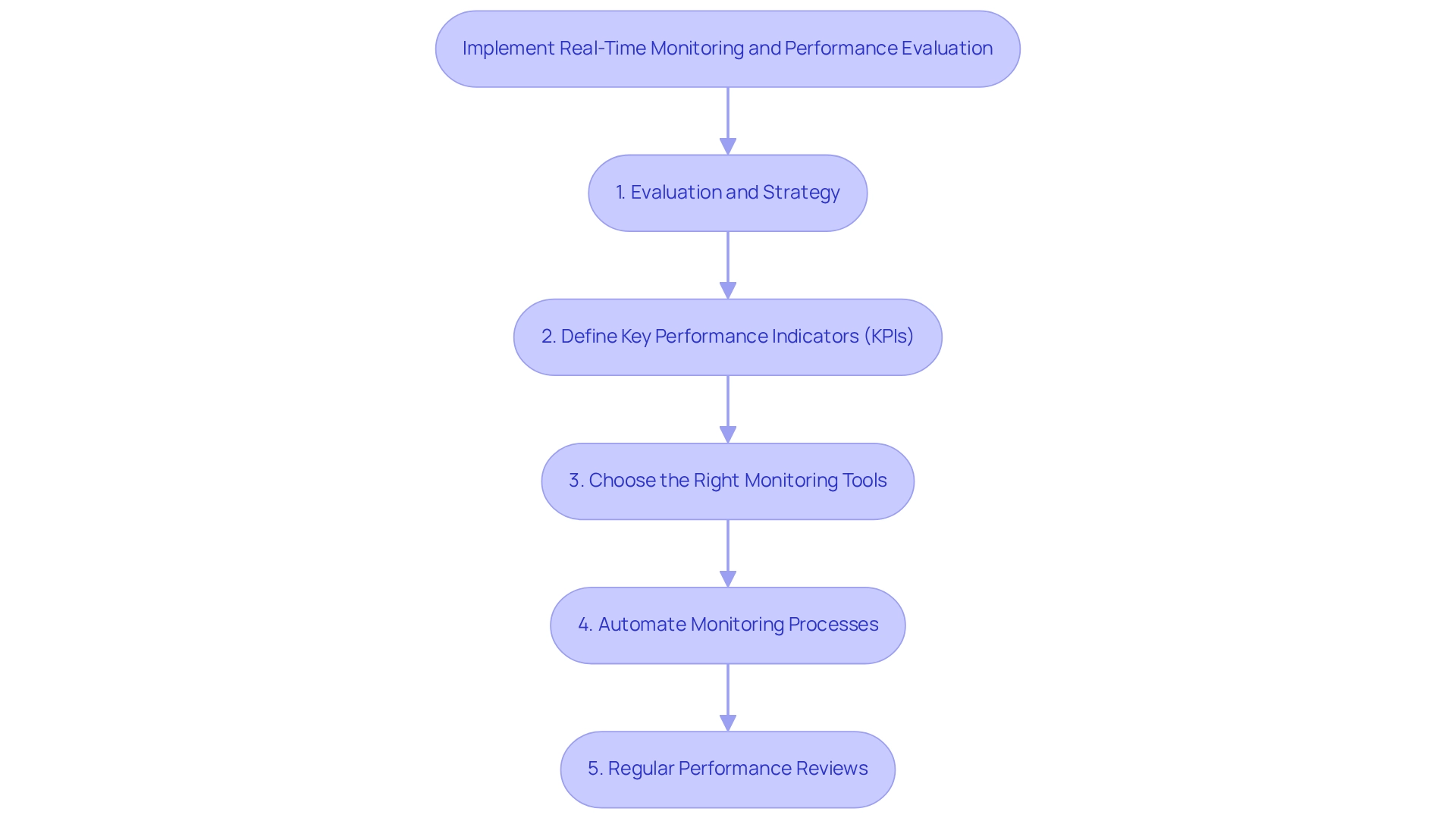
Implement Real-Time Monitoring and Performance Evaluation
Implementing real-time monitoring and performance evaluation is not just beneficial; it is essential for the integration of computer systems and optimizing their performance. To achieve this, we propose the following essential steps:
- Evaluation and Strategy: We begin with a comprehensive evaluation of our existing setups, identifying areas that would benefit most from real-time monitoring. This foundational step is crucial for aligning our monitoring strategies with our business objectives.
- Define Key Performance Indicators (KPIs): We establish KPIs that align with our business objectives, focusing on metrics such as operational uptime, response durations, and information accuracy. These indicators are vital for assessing overall business performance and guiding our strategic decisions. As noted by Hazal Şimşek, improved customer satisfaction can be achieved by tracking workflow for customer lifetime value, underscoring the importance of KPIs in enhancing our operational effectiveness.
- Choose the Right Monitoring Tools: We select tools that provide extensive visibility into performance. Efficient monitoring solutions should offer alerts for irregularities and support historical data examination, allowing us to proactively manage overall health. Avato’s hybrid integration platform is specifically designed to support such monitoring capabilities, ensuring that we can maintain 24/7 uptime and reliability.
- Automate Monitoring Processes: We leverage automation to streamline our monitoring tasks. Automated alerts can promptly notify our teams of performance issues, enabling swift responses and minimizing potential disruptions. This is especially crucial in sectors such as banking and healthcare, where the reliability of our infrastructure is paramount.
- Regular Performance Reviews: We conduct periodic evaluations of our performance against the established KPIs. These assessments provide insights that guide our choices related to system enhancements and implementations, ensuring the ongoing advancement of our operational capabilities. By utilizing Avato’s platform, we can implement a phased strategy for modernization, minimizing risks and enhancing adaptability.
In 2025, we increasingly recognize the importance of real-time monitoring, with many of us adopting advanced tools that support these practices. For instance, a logistics company recently identified 70% compliance risks in its credit and collections management process through effective monitoring strategies. This highlights the potential for similar outcomes in the banking sector, where Avato’s hybrid integration platform can facilitate enhanced monitoring and performance evaluation. By implementing these best practices, we can significantly enhance our operational efficiency and ensure that the integration of computer systems functions at optimal levels.
Conclusion
In today’s rapidly evolving digital landscape, we must prioritize robust security protocols, streamlined integration processes, and real-time performance monitoring to stay competitive. Establishing effective security measures—such as data encryption, access controls, and regular audits—ensures that sensitive information is safeguarded against ever-evolving threats. By leveraging solutions like Avato’s Hybrid Integration Platform, we not only mitigate risks but also enhance system interoperability, allowing us to maximize the value of our legacy systems.
Streamlining the integration of legacy systems through middleware solutions, API development, and incremental integration is essential for maintaining operational continuity while modernizing our processes. This structured approach reduces risks and enhances customer engagement, which is crucial in sectors like banking and healthcare, where customer trust and satisfaction are paramount.
Furthermore, implementing real-time monitoring and establishing clear performance indicators enable us to proactively manage system health and operational efficiency. By embracing these strategies, we can navigate the complexities of digital transformation and unlock new opportunities for growth and innovation. Our collective efforts to enhance cybersecurity, streamline integrations, and optimize performance will not only safeguard data integrity but also foster a culture of resilience and adaptability in an increasingly digital world.
What steps will you take to ensure your organization thrives in this new era?