Overview
We recognize the critical importance of mastering application orchestration in banking to enhance compliance and security. By automating and integrating various applications and services, we can streamline processes, meet regulatory requirements, and implement robust security measures. This strategic approach not only improves operational efficiency but also elevates the customer experience.
What’s holding your team back from achieving these advancements? Embracing this integration is not just beneficial; it is essential for staying competitive in today’s landscape. Let us partner together to harness the power of application orchestration and transform your operations.
Introduction
In the rapidly evolving landscape of banking, we recognize that application orchestration is not just a strategy; it is a transformative approach that enables financial institutions to streamline operations and enhance service delivery. By automating the coordination of various applications and integrating disparate systems, we can achieve operational efficiency and maintain compliance in a complex regulatory environment.
What challenges are you facing in your current operations?
This article delves into the significance of orchestration in banking, exploring how it addresses compliance challenges, fortifies security protocols, and facilitates the seamless integration of legacy systems. With a focus on best practices and innovative strategies, we highlight the vital role that orchestration plays in shaping the future of banking and improving customer experiences.
Join us as we explore how embracing orchestration can elevate your institution’s capabilities and drive success.
Define Application Orchestration in Banking
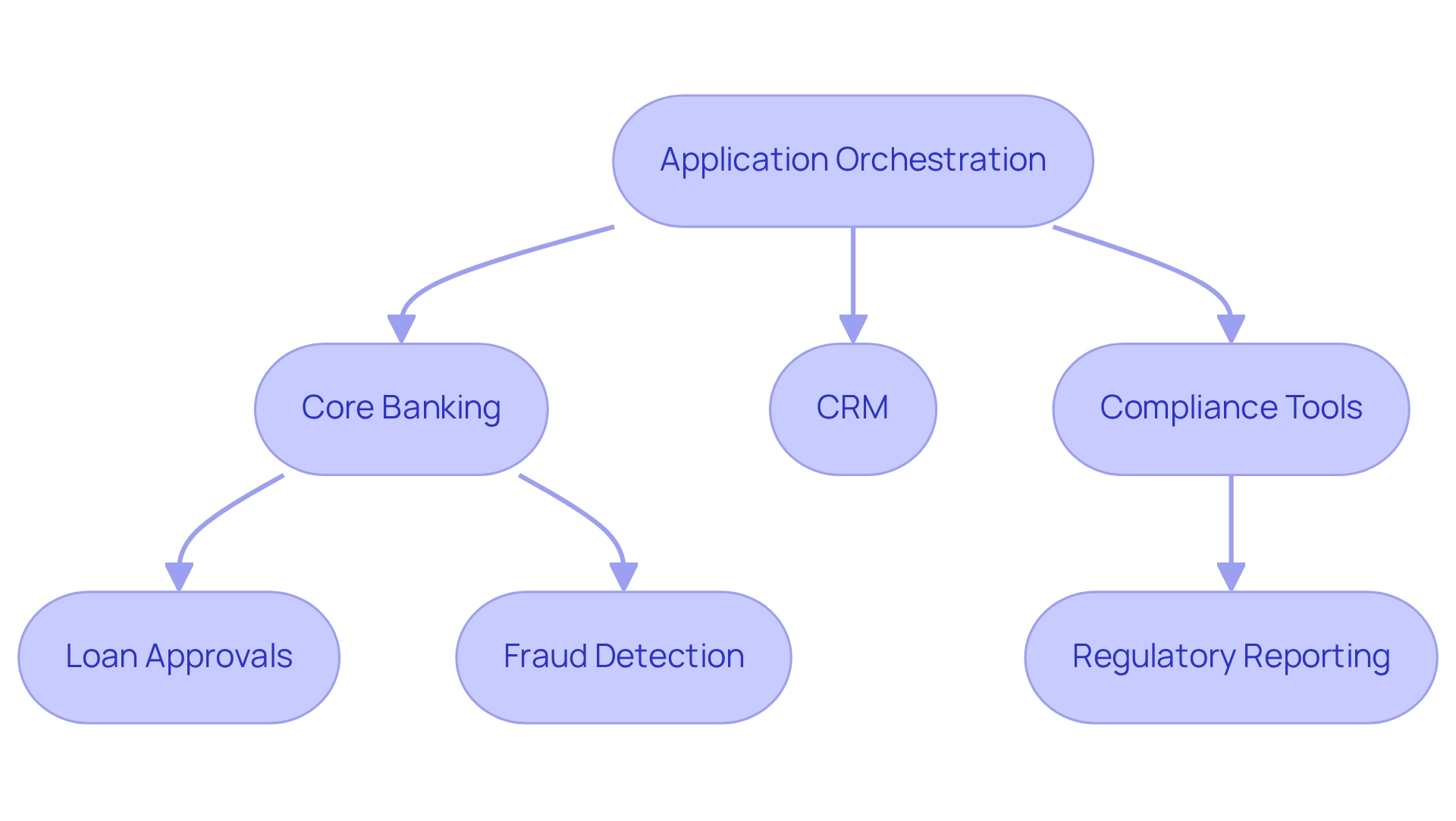
In banking, application orchestration is not just a trend; it is a critical strategy for automating the coordination of various applications and services aimed at streamlining processes and enhancing operational efficiency. We recognize that this approach enables us to integrate disparate systems—such as core banking, customer relationship management (CRM), and compliance tools—into a cohesive workflow.
By employing application orchestration, we can automate complex processes like loan approvals, fraud detection, and regulatory reporting, ensuring seamless communication between platforms and an uninterrupted flow of information. This integration is essential for meeting regulatory requirements and significantly enhances customer experiences by delivering timely and accurate services.
As Inese noted, through a strategic and forward-thinking UX approach, we can elevate user engagement and financial management, akin to the innovative solutions offered by the Liv ecosystem. Furthermore, the case study titled ‘Winning in the Digital Banking Landscape’ underscores the necessity for banks to leverage customer data to provide personalized services, positioning ourselves as intimate partners in our customers’ financial futures.
This aligns with the key insight that the future of banking revolves around understanding our customers’ financial lifestyles. With Avato’s dedicated hybrid integration platform, we can unlock isolated assets and maximize the value of legacy systems, ensuring 24/7 uptime for critical integrations. This reliability empowers us to depend confidently on our application orchestration capabilities to maintain operational continuity and compliance in an increasingly complex digital landscape.
Jamie Dimon asserts that mastering technology is vital for future success, reinforcing the significance of application management in achieving these objectives.
Address Compliance Challenges in Application Orchestration
Compliance challenges in application management are fundamentally driven by the necessity to adhere to a myriad of regulations, including GDPR, PCI DSS, and anti-money laundering (AML) laws. To navigate these complexities effectively, we must adopt the following best practices:
-
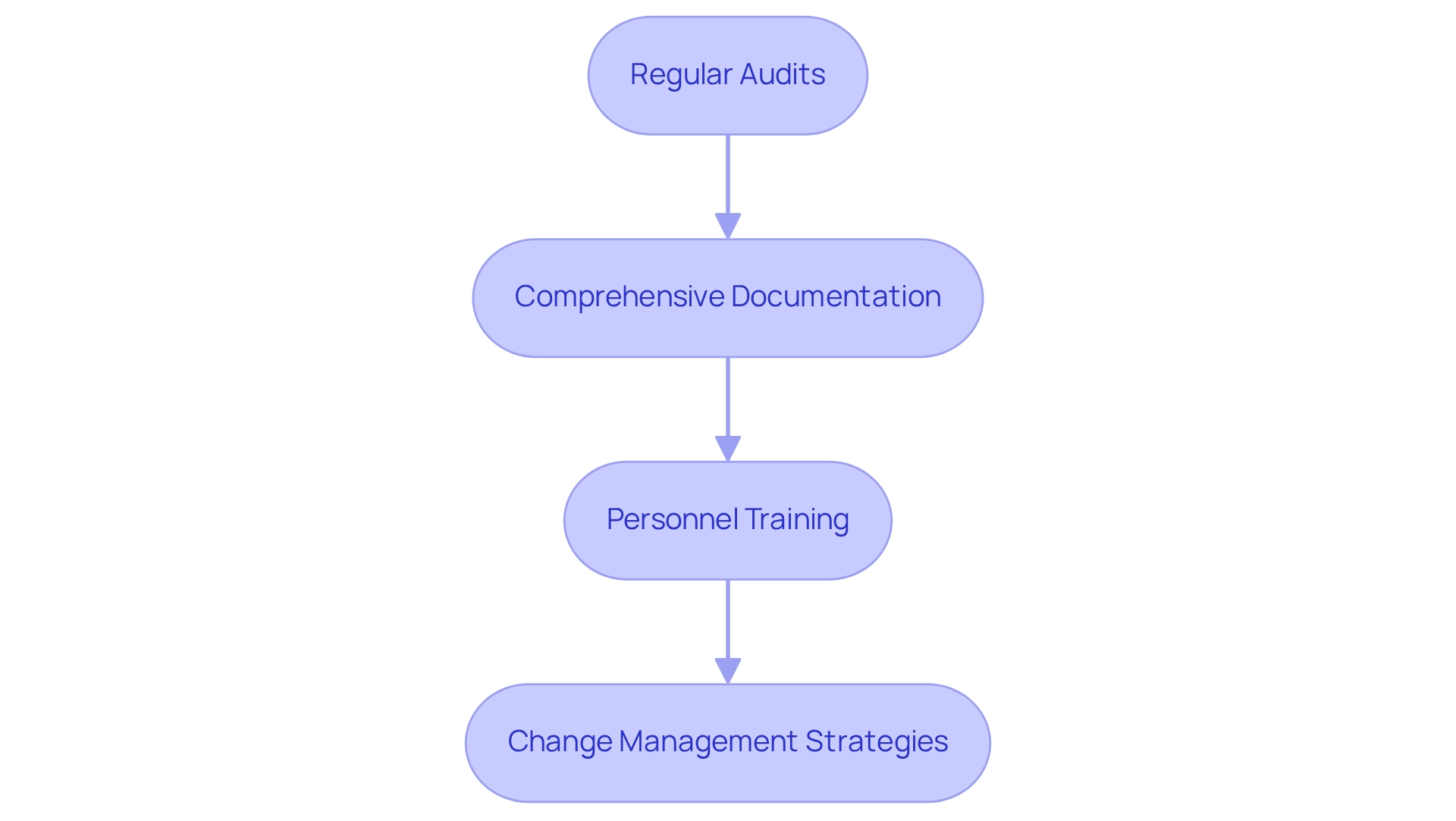
First and foremost, regular audits and assessments of application orchestration processes are essential to ensure adherence to regulatory standards. This involves a thorough review of data handling practices and access controls to identify potential vulnerabilities. Considering that 68% of respondents from the regulatory division feel inadequately equipped for the demands placed on them, regular audits can assist us in effectively prioritizing resource allocation. Furthermore, implementing automated regulatory oversight through tools that provide real-time monitoring of adherence metrics enables us to swiftly identify and rectify any deviations from regulatory requirements, thereby minimizing risks related to non-conformity. For instance, using tools that allow rapid creation of reports can greatly alleviate documentation burdens and satisfy auditors.
-
In addition, maintaining comprehensive documentation of all application orchestration processes and decisions is crucial. This practice not only aids in meeting regulations but also establishes a clear audit trail for regulatory reviews. It is especially vital as numerous organizations encounter difficulties in managing third-party risks, with approximately 25% possessing a third-party risk management budget below $50,000, suggesting possible weaknesses in adherence efforts.
-
Moreover, investing in extensive training initiatives for personnel on regulatory demands and the importance of following set procedures within workflow processes cultivates a culture of adherence throughout our organization. Implementing change management strategies is also vital to smooth the transition to new systems and processes. This is particularly critical given that 54% of organizations have faced a cyberattack in the past year, highlighting the necessity for strong security measures and knowledgeable staff.
By adopting these best practices, including regular audits and automated compliance monitoring together with training and change management, we can more effectively handle compliance challenges in application orchestration, ensuring we fulfill regulatory requirements while enhancing our operational capabilities.
Implement Robust Security Protocols
To ensure the security of application orchestration in banking, we must adopt essential protocols that address the complexities of our digital landscape.
-
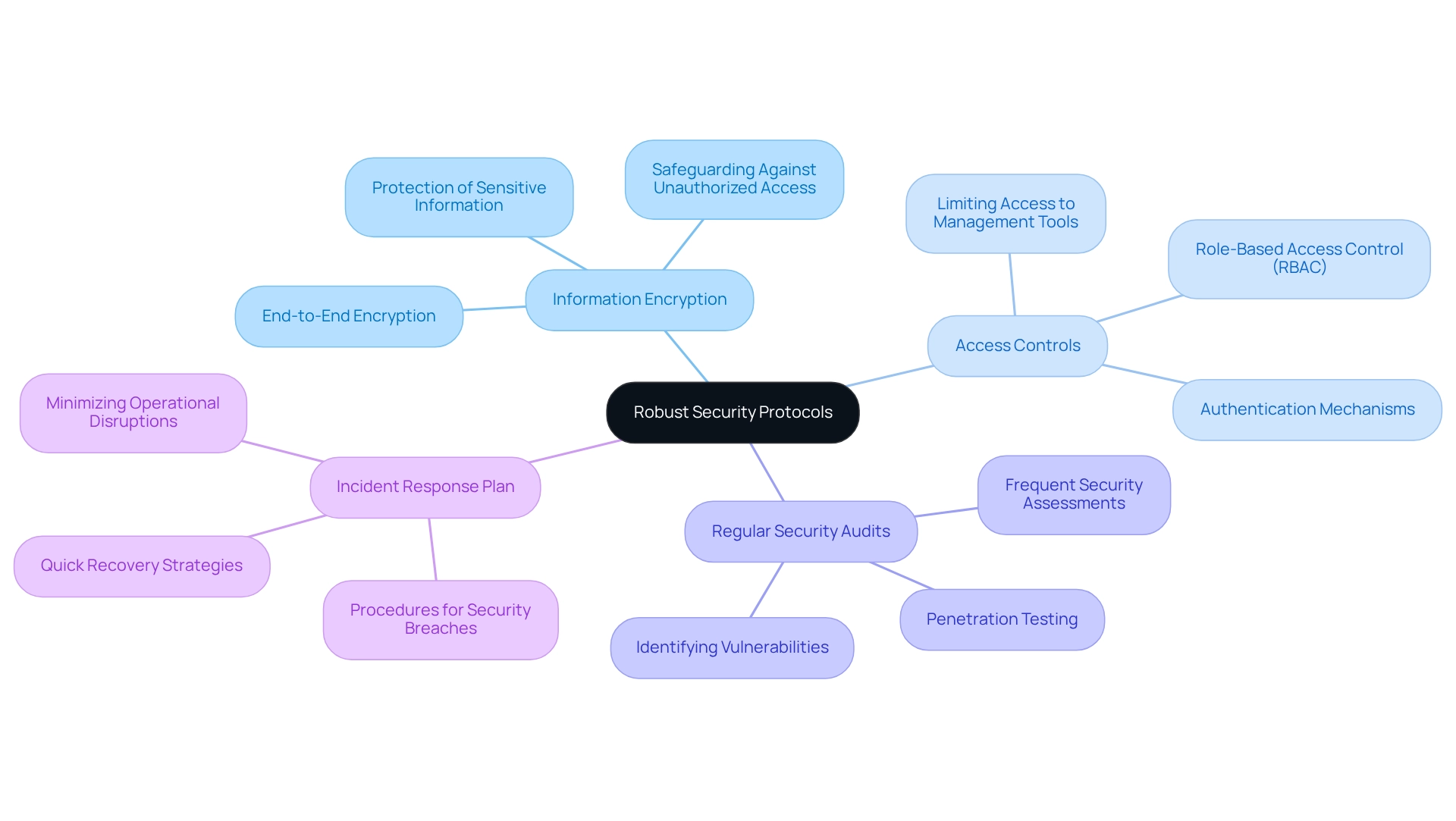
Information Encryption: We advocate for the implementation of end-to-end encryption for information both in transit and at rest. This practice is crucial for safeguarding sensitive information against unauthorized access, particularly as we manage approximately 15,000 exposures across our environments.
-
Access Controls: Establishing stringent access controls and authentication mechanisms is vital to limit access to management tools and data. Role-based access control (RBAC) serves as an effective strategy for managing permissions, ensuring that only authorized personnel can interact with our critical systems.
-
Regular Security Audits: Conducting frequent security assessments and penetration testing allows us to uncover vulnerabilities within our application orchestration framework. Proactively identifying and remediating these weaknesses is essential for maintaining a robust security posture.
-
Incident Response Plan: We must create and uphold a thorough incident response plan that outlines procedures for addressing security breaches or information leaks. This plan should facilitate quick recovery and minimize operational disruptions, reinforcing our resilience against cyber threats.
As Patrick Harr, CEO at SlashNext, highlights, “Cybersecurity Awareness Month serves as a reminder that the tactics employed by cyber-criminals keep changing, making it essential for organizations to possess the resources and strategies necessary to avert these attacks before they lead to information breaches and other security issues.” This underscores the importance of the protocols we advocate.
Additionally, Boaz Gorodissky, CTO at XM Cyber, emphasizes the need for a comprehensive approach to managing cybersecurity exposures, stating that we must adopt proactive strategies that provide a continuous view of our critical assets to safeguard against complex threats.
By implementing these protocols, we can significantly enhance our security measures, ensuring compliance and protecting sensitive data within an increasingly complex digital landscape. What’s holding your team back from adopting these essential practices?
Integrate Legacy Systems Seamlessly
Incorporating legacy technologies into our application orchestration framework is essential for modern banking operations, albeit with significant challenges. To facilitate this integration effectively, we advocate for the following best practices:
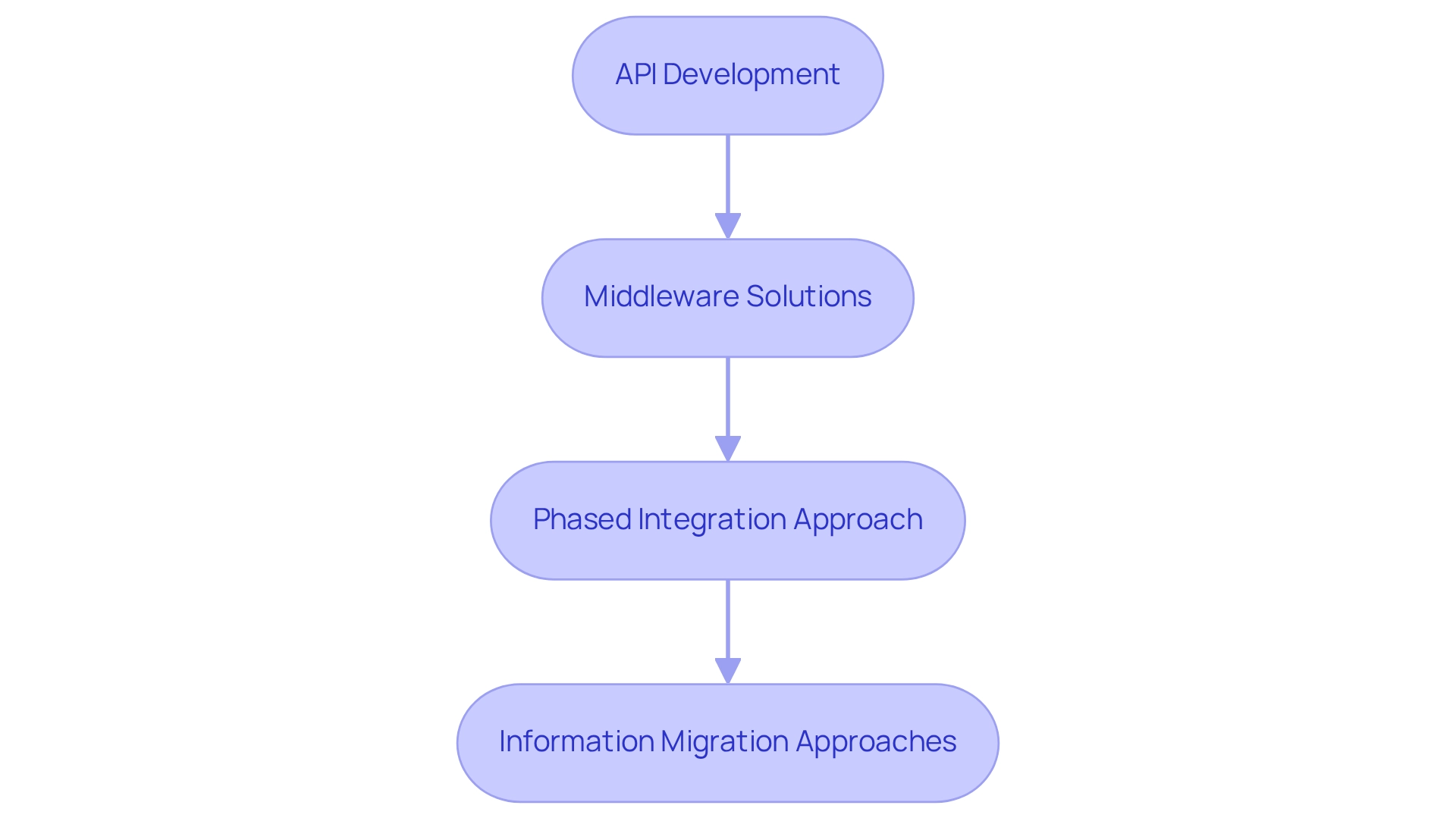
- API Development: We create robust APIs that enable older platforms to communicate seamlessly with modern applications. This decoupling enhances information exchange and operational efficiency.
- Middleware Solutions: Our use of Avato’s specialized hybrid integration platform links legacy frameworks with new applications, ensuring compatibility and facilitating seamless information flow across platforms. Avato’s architecture is designed for secure transactions, making it a trusted choice for banks.
- Phased Integration Approach: We adopt a phased integration strategy, commencing with less essential components. This minimizes disruption and allows for a gradual transition of more critical functions, thereby reducing risks associated with migration.
- Information Migration Approaches: We formulate thorough information migration strategies that uphold integrity and accessibility throughout the integration process. This may involve information purification and alteration to align with the requirements of new frameworks.
As we navigate the complexities of merging outdated infrastructures, it is crucial to recognize that 69% of respondents perceive hazards linked to transitioning to advanced technologies as obstacles to implementing next-generation solutions. However, successful case studies demonstrate that overcoming these challenges can unlock significant business insights and operational efficiencies. For instance, addressing data silos from outdated technologies can enhance communication within our organizations, leading to better alignment and the realization of missed business opportunities. By implementing these best practices, we can ensure a smoother transition to modern application orchestration, ultimately enhancing compliance and security. As Gustavo Estrada noted, Avato simplifies complex projects and delivers results within desired time frames and budget constraints, underscoring the effectiveness of these integration strategies. Furthermore, while the journey to AI adoption is challenging for banks with legacy systems, the benefits make it worthwhile, highlighting the urgency of these integration practices.
Conclusion
Embracing application orchestration is not just beneficial; it is essential for banks that seek to thrive in a digital-first landscape. By automating the coordination of various applications and integrating legacy systems, we can significantly enhance operational efficiency and improve customer experiences. Our insights underscore the critical need to address compliance challenges, implement robust security protocols, and seamlessly integrate legacy systems to ensure a resilient and agile banking environment.
The necessity for regular audits, automated compliance monitoring, and comprehensive training programs cannot be overstated. These practices not only help us adhere to complex regulatory requirements but also foster a culture of compliance that is vital in today’s ever-evolving digital landscape. Furthermore, implementing strong security measures—such as data encryption and access controls—is vital to protect sensitive information and maintain customer trust.
Ultimately, the integration of legacy systems through effective strategies, such as API development and phased approaches, can unlock new operational efficiencies and insights. As we navigate these transformative changes, the strategic adoption of application orchestration will be key to driving innovation and ensuring long-term success in the competitive banking sector. It is clear that the future of banking hinges on our ability to harness orchestration, paving the way for enhanced service delivery and fortified customer relationships.

