Overview
We recognize that achieving success in application development integration hinges on four essential practices.
- First, we must establish robust compliance and security standards to safeguard our processes.
- Next, effectively integrating legacy systems is crucial; this not only preserves valuable data but also streamlines operations.
- Furthermore, implementing real-time monitoring and alerts allows us to proactively address issues before they escalate.
- Finally, fostering cross-departmental collaboration enhances our collective efforts, ensuring that all teams work in harmony towards common goals.
These practices are not merely theoretical; they are supported by evidence and real-world examples that demonstrate their significance. By adhering to these key strategies, we can ensure secure, efficient, and collaborative integration processes that align with regulatory requirements and significantly enhance our organizational performance.
What’s holding your team back from fully realizing these benefits? Together, we can navigate the complexities of integration and implement these proven practices to drive our success forward.
Introduction
In the rapidly evolving landscape of digital transformation, we recognize that the integration of applications across various sectors has become a critical focus for organizations seeking to enhance operational efficiency and security. As we navigate the complexities of compliance, legacy systems, and real-time monitoring, establishing robust frameworks and fostering collaboration emerge as essential strategies.
This article delves into the foundational steps necessary for successful application integration, underscoring the importance of:
- Security standards
- Effective legacy system integration
- Real-time performance monitoring
- Cross-departmental collaboration
By embracing these strategies, we can safeguard sensitive data, drive innovation, and maintain a competitive edge in our respective industries. What’s holding your team back from achieving these goals?
Establish Compliance and Security Standards
To achieve successful application unification, we must prioritize the establishment of robust compliance and security standards. This begins with a thorough understanding of pertinent regulations such as GDPR, HIPAA, and PCI-DSS, ensuring that all our development practices are meticulously aligned with these requirements. Adopting a security-first approach is essential; this means integrating security measures throughout the entire development lifecycle—from initial planning to final deployment. Regular audits and assessments are crucial for maintaining compliance and adapting to evolving regulations.
Our secure hybrid integration platform is designed for secure transactions, establishing it as a reliable solution for banks, healthcare, and government sectors. With a focus on 24/7 uptime and reliability, we deliver a rock-solid foundation for digital transformation initiatives, ensuring that there is no room for defects, errors, or outages. For instance, a financial organization might adopt multi-factor authentication and advanced encryption methods to protect sensitive customer information, thereby building trust and improving security within their systems. Moreover, with 27% of security and IT experts recognizing internal audit fatigue as a major compliance obstacle, we must optimize our processes to address this issue effectively. Strategies to address this include automating audit processes and providing ongoing training for our staff to ensure they are well-versed in compliance requirements.
The urgency of establishing these standards is underscored by the fact that the average cost of a data breach per incident in 2021 reached $4.24 million, highlighting the financial risks associated with non-compliance. Additionally, insights from the case study titled “Obstacles to Compliance Confidence” reveal that a lack of knowledgeable personnel and inadequate resources are significant barriers to achieving compliance. By establishing clear compliance frameworks and security protocols, we can navigate the complexities of regulatory requirements while ensuring the integrity and safety of our application development integration.
In summary, we should:
- Understand and align with GDPR, HIPAA, and PCI-DSS regulations.
- Integrate security measures throughout the development lifecycle.
- Conduct regular audits and assessments.
- Implement multi-factor authentication and encryption protocols.
- Streamline processes to mitigate internal audit fatigue.
- Address knowledge gaps and resource limitations to enhance compliance confidence.

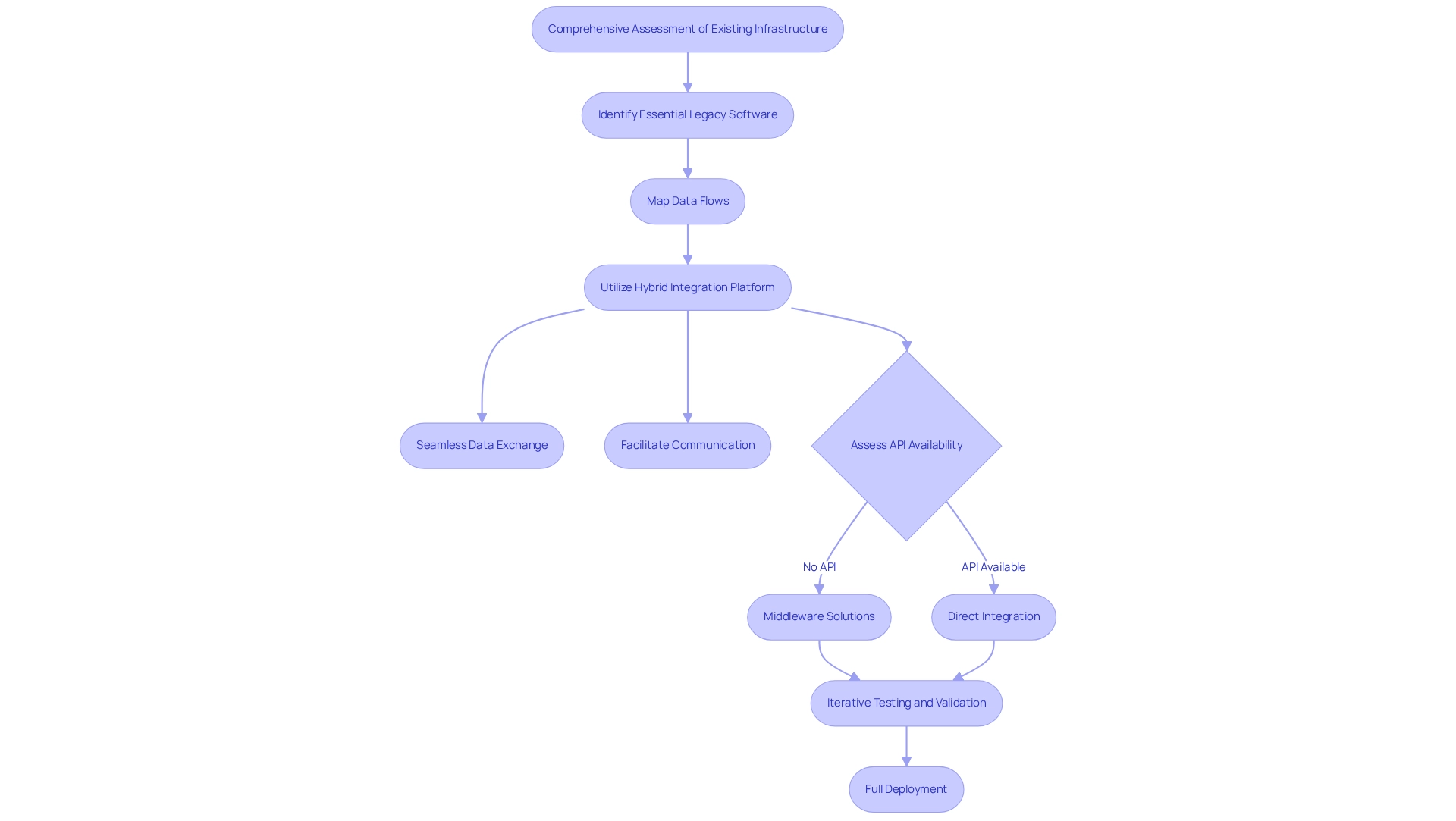
Integrate Legacy Systems Effectively
To effectively integrate legacy systems, we must begin with a comprehensive assessment of our existing infrastructure. This involves identifying essential legacy software and mapping their data flows. Our Hybrid Integration Platform plays a crucial role in supporting application development integration by facilitating communication between legacy systems and modern applications, enabling seamless data exchange. For instance, a healthcare provider could utilize our platform to link an outdated patient management system with a modern electronic health record (EHR) system, ensuring that patient data remains accessible and up-to-date across all platforms.
Statistics indicate that almost half of legacy systems do not have APIs, creating considerable difficulties, especially in the banking and healthcare industries where secure and dependable connectivity is crucial. This underscores the necessity of middleware solutions like our Hybrid Integration Platform to bridge the gap between old and new technologies. By streamlining intricate processes and offering real-time oversight and notifications on system performance, we can notably lower expenses while improving operational efficiency. As such, prioritizing gradual migration strategies is essential to minimize disruption. This approach allows for iterative testing and validation of integrations, ensuring that systems work harmoniously before full deployment.
Inna Fishchuk, a Market Data Analyst, emphasizes, “Each decision to upgrade or replace should be based on a thorough assessment of the legacy solution, the entity’s specific needs, budget, and long-term goals.” This highlights the importance of a careful evaluation process.
Moreover, the case study titled “Security Risks of Legacy Healthcare Systems” illustrates that legacy systems can pose significant security risks due to vulnerabilities that cannot be adequately mitigated through upgrades. Healthcare entities must prioritize replacing high-risk legacy systems to safeguard sensitive patient information and adhere to contemporary cybersecurity standards.
Furthermore, the expanding talent pool for contemporary technologies such as cloud computing and AI simplifies the task for businesses to locate developers who can aid in the modernization process. By implementing these strategies, we can manage the challenges of legacy system unification while improving operational efficiency and security through application development integration.
Implement Real-Time Monitoring and Alerts
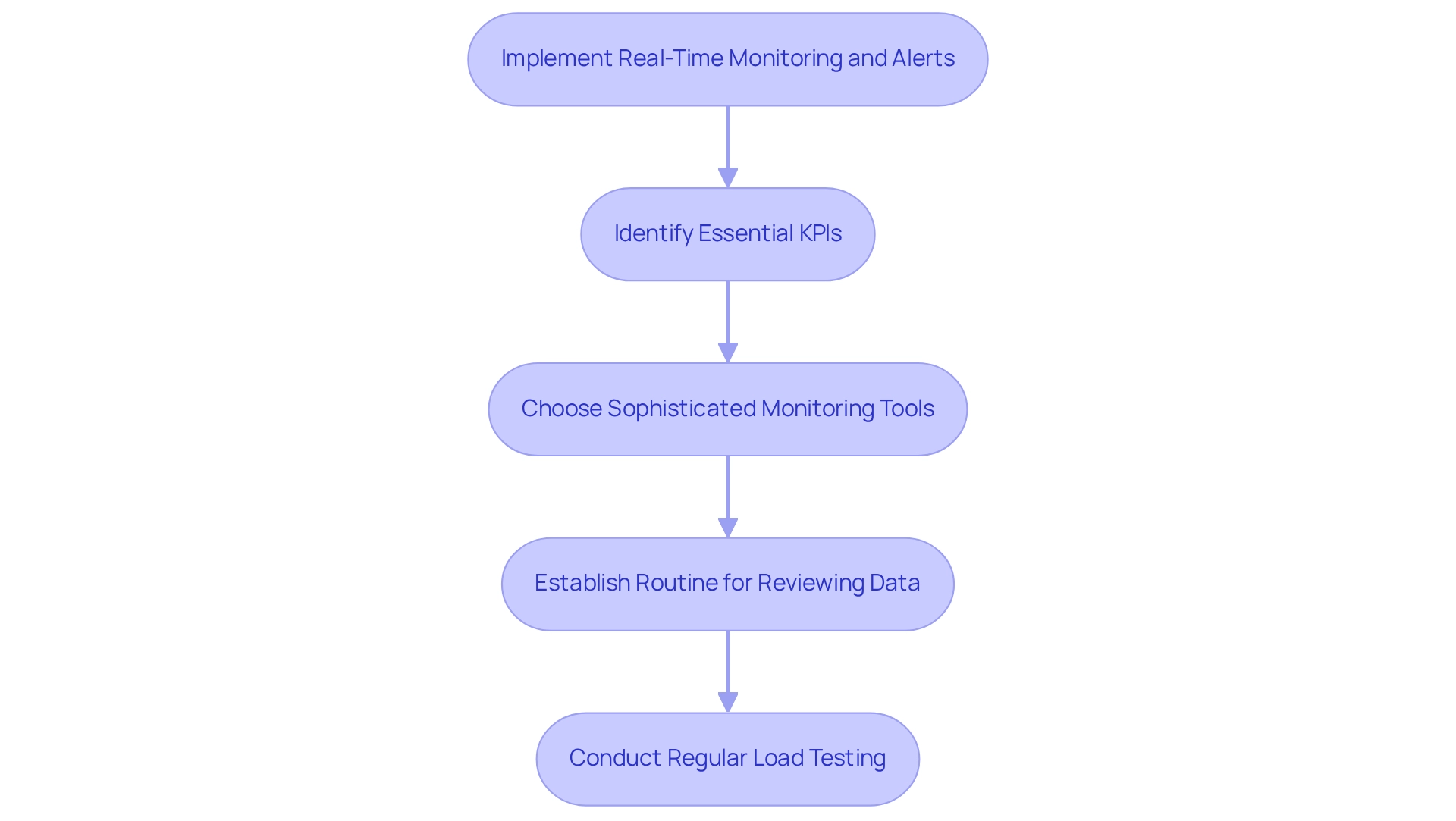
Establishing real-time monitoring and notifications is essential for organizations like ours aiming to maintain optimal software performance and application development integration efficiency, particularly within the framework of a secure hybrid integration platform designed for safe transactions and 24/7 availability. This process involves creating systems that continuously track key performance indicators (KPIs) such as response times and error rates, which are vital for evaluating overall application performance. By leveraging advanced monitoring tools equipped with dashboards and alerting capabilities, we can swiftly identify and rectify issues before they escalate into significant problems.
For instance, a financial institution utilizing our platform may implement a monitoring solution that promptly alerts IT personnel to transaction processing delays. This proactive approach empowers us to investigate and resolve issues quickly, minimizing potential disruptions. Moreover, regular reviews of monitoring data not only facilitate immediate troubleshooting but also inform our ongoing optimization efforts, ultimately enhancing system performance and ensuring the reliability that we are known for in the banking, healthcare, and government sectors.
Current trends in real-time monitoring underscore the importance of tracking various performance metrics to ensure a seamless user experience. By 2025, organizations are increasingly adopting advanced tools like AI-driven monitoring solutions that provide insights into software behavior, enabling more informed decision-making. Notably, statistics reveal that 60% of developers report increased productivity due to these AI-driven solutions, translating into faster response times and improved service delivery for banking IT managers.
Expert opinions highlight that increased latency directly impacts load times, making it imperative for organizations to prioritize real-time monitoring. Joydip Kanjilal, a developer and author, emphasizes that ‘higher latency has a direct effect on the load time of a program,’ reinforcing the necessity for effective KPI monitoring.
To implement real-time monitoring and alerts effectively, we recommend the following steps:
- Identify essential KPIs pertinent to software performance and application development integration.
- Choose sophisticated monitoring tools that provide real-time insights and alerting features, preferably integrated with our platform.
- Establish a routine for reviewing monitoring data to facilitate ongoing optimization.
- Conduct regular load testing to evaluate system scalability and performance under heavy traffic.
By concentrating on KPIs relevant to software connectivity and utilizing our specialized hybrid linkage platform, we can ensure that we meet user requirements efficiently while enhancing our competitive advantage.
Foster Cross-Departmental Collaboration
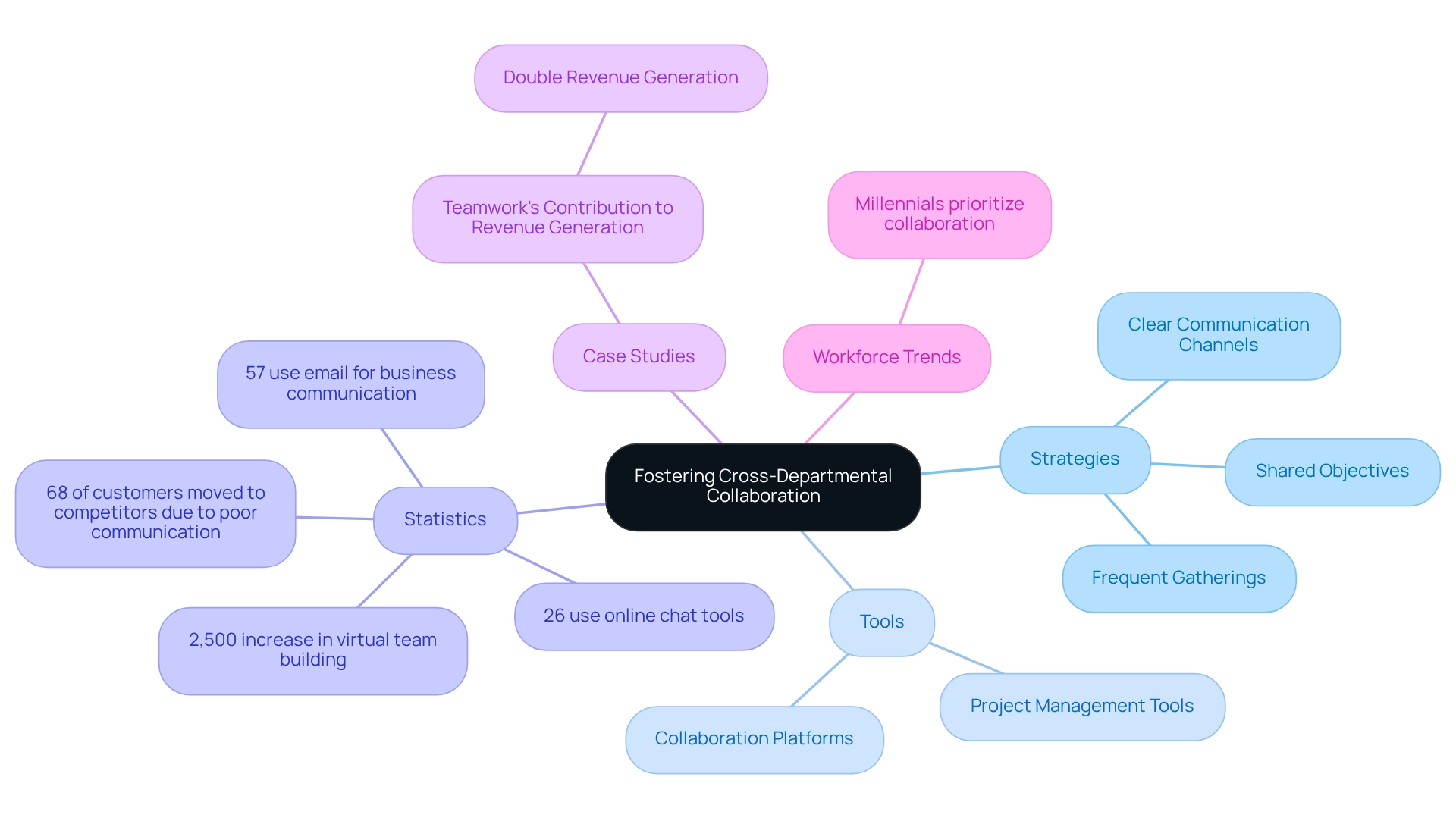
Encouraging interdepartmental cooperation is vital for successful application development integration and implementation, especially in environments where 24/7 uptime is crucial. We must establish clear communication channels and shared objectives among our teams. Frequent gatherings and workshops that bring together stakeholders from IT, operations, compliance, and business units are essential for discussing collaboration strategies and tackling challenges.
The implementation of collaboration tools, such as project management platforms, can significantly enhance information sharing and project tracking. For instance, a government organization could leverage such a platform to allow various departments to participate in planning and execution, ensuring diverse viewpoints are incorporated into the process. This collaborative approach not only enhances the quality of connections but also fosters a culture of teamwork and innovation.
Our hybrid platform simplifies this by streamlining complicated connections and lowering expenses, enabling our teams to concentrate on strategic goals. Significantly, we provide assistance for 12 tiers of interface maturity, which improves our amalgamation strategies by balancing speed and sophistication.
Statistics reveal that:
- 57% of individuals utilize email for business correspondence
- 26% employ online chat tools
This underscores the significance of efficient communication tools in achieving our collaboration objectives. Furthermore, a notable 2,500% increase in companies investing in virtual team building highlights the growing recognition of collaboration’s value.
Case studies indicate that entities investing in team collaboration can witness revenue generation increases of up to 100%, demonstrating the tangible advantages of nurturing a collaborative environment in application development integration. Additionally, with 68% of customers moving to competitors in 2025 due to poor business communication skills, the need for effective communication in integration projects is critical.
Lastly, as nearly half of the U.S. workforce consists of Millennials who prioritize workplace collaboration, fostering a collaborative environment is increasingly relevant for modern organizations, particularly when leveraging our dedicated platform to enhance operational visibility and issue resolution.
Conclusion
In conclusion, we recognize that effective application integration is paramount for organizations striving to enhance operational efficiency and security. By establishing robust security standards, we safeguard sensitive data and navigate complex regulations such as GDPR, HIPAA, and PCI-DSS. Our commitment to embedding security measures throughout the development lifecycle, coupled with regular audits, significantly reduces the risk of costly data breaches.
Furthermore, integrating legacy systems is essential for ensuring seamless data flow and continuity. Our middleware solutions, including Avato’s Hybrid Integration Platform, facilitate communication between outdated and modern applications, thereby improving both efficiency and security. A thorough assessment of existing infrastructure allows us to support strategic modernization with minimal disruption.
Real-time monitoring and alerts are critical for maintaining optimal application performance. By focusing on key performance indicators and utilizing advanced monitoring tools, we can swiftly identify and address issues, ensuring reliability and a smooth user experience.
In addition, fostering cross-departmental collaboration strengthens our integration efforts. By encouraging teamwork across IT, operations, compliance, and business units, we enhance communication and drive innovation. Implementing collaboration tools and conducting regular stakeholder meetings cultivates a culture of shared objectives, leading to more effective integration strategies.
Ultimately, by prioritizing security standards, effectively integrating legacy systems, implementing real-time monitoring, and promoting collaboration, we can protect our operations, drive innovation, and maintain a competitive edge in a rapidly evolving digital landscape. Addressing these key areas will unlock the full potential of application integration and empower our teams to overcome challenges efficiently.

